Home Lab VPN
Introduction
VPN (Virtual Private Network) is a service that creates a secure, end-to-end encrypted connection between the host and the internet. Using routing to send traffic to a remote server, this will use the remote server external IP address and encrypt the data being sent across the network. Using a VPN has many benefits that would reduce the risks to your privacy and security, this works by:
- Encryption: typically, the traffic going through the VPN will be encrypted e.g. if an attacker intercepts the traffic, they shouldn’t be able to read the data.
- IP Masking: this replaces your external IP address with the end service external IP address. This would hide would hide your actual IP address and geographic location.
- Secure Tunnel: end-to-end encryption creates a secure tunnel that reduces the risks of exposing internet activities e.g. sensitive information.
Goals
Using my Dell Wyse (pvewyse1), I plan on setting up PIVPN which allows open-source protocol WireGuard or OpenVPN to run a secure tunnel to the system, I will be using WireGuard due to it being having better performance, modern cryptography and simpler to configure. I want to achieve the following with this solution:
- I do a lot of travelling and found that it would be useful to connect back to my home lab to remotely access resources on the go.
- In situations where I do need to connect to public/unsecure WiFi networks I can use the VPN to encrypt my traffic to mitigate the risks of packet capturing.
Setup
On the host you want the VPN services to run on:
- Install PiVPN:
sudo curl -L https://install.pivpn.io | bash. - Follow the steps on screen: Choose between WireGuard or OpenVPN (I will be using WireGuard for the reasons mentioned above).
- Set your static IP address or use Dynaminc DNS (DDNS).
- Setup port forwarding for
51820 UDP, this will need to be configured on your router or firewall. - Create a client .conf profile this be transferred to the client device you want to connect from:
pivpn -a {hostname}. - Check the .conf file has been created:
cd /home/{username}/configs && ls -a. - Use a file transfer solution e.g. WInSCP, to copy the .conf to the client device.
On a Unix client device you want to connect to the VPN on:
- Move the .conf file to:
/etc/wireguard/{hostname}.conf - Start the VPN connection:
sudo wg-quick up {hostname} - Check the status of the VPN connection:
sudo journalctl -u wg-quick@{hostname}
You can start the VPN automatically on boot using:
sudo systemctl enable wg-quick@{hostname}thensudo reboot, after restarting the system the VPN will start on boot. To disconnect from the VPN use:sudo wg-quick down {hostname}
On a Windows client device you want to connect to the VPN on:
- Install WireGuard here.
- Click Add tunnel > Import tunnel from file > select the {hostname}.conf file.
- VPN functionality can be controlled by the UI.
Outcome
I have the client installed on my laptop and mobile with the VPN automatically tuned on it always me to easily access my home lab to work on projects remotely. The setup has been a simple process and has given me a lot of flexibility when working on the go and the privacy and security when working on unknown or unsecure networks. Also, it’s very easy to scale up or down the amount of connections when required. In the future I will see if I can enhance the security harderning standards on the virtual machine that is running the VPN services, this would mitigate any potential risk of authorised access through the VPN. The example below shows the VPN tunnel log between my laptop and the server with PiVPN installed, allowing me to connect to my proxmox console remotely. 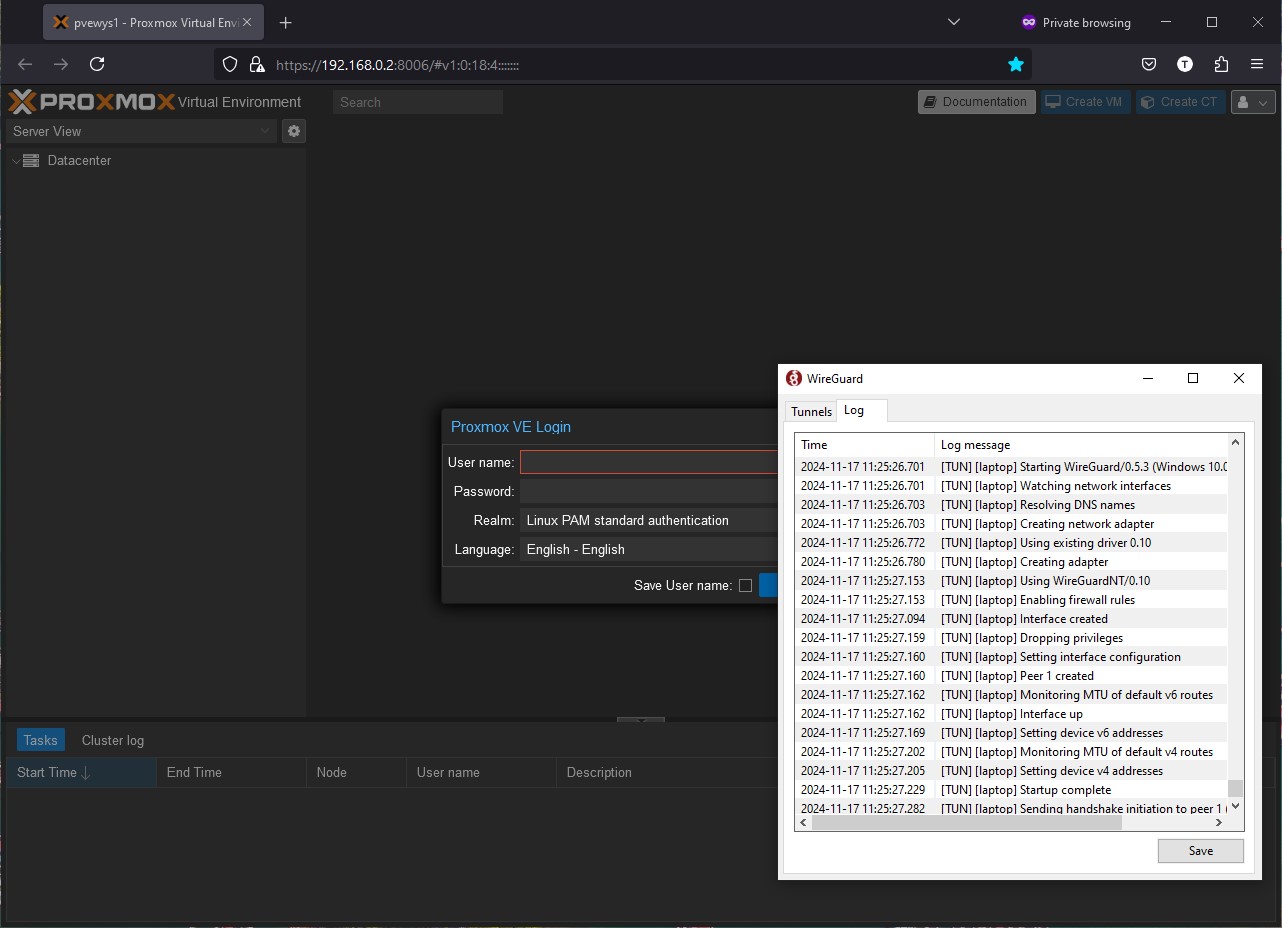
Useful links: