Rise of QR Phishing
QR Phishing
Known as Quishing is the practice of using QR scanning to redirect victims to a malicious site or program. This can be done virtually on messaging services/emails or physically on information boards/posters.
The use of QR codes is becoming more common for accessing websites, media, information as well as used to authenticate account logins. Consequently, users are at risk of mistaken phishing QR codes for legitimate codes.
Due to the QR code hiding the URL, it can be used to bypass email filters. Allowing for malicious QR codes to evade email security systems. Therefore, it is best practice to implement Quishing training and email simulations across your organisation.
Examples
- Microsoft Credentials Quishing Attackers send phishing emails containing QR codes mimicking Microsoft Authenticator emails used for authentication services. The QR code will redirect the user to a fake Microsoft site where they will be advised to enter their Microsoft Credentials. This attack is becoming more common due to the ease and potential gain for private or confidential information of an account.
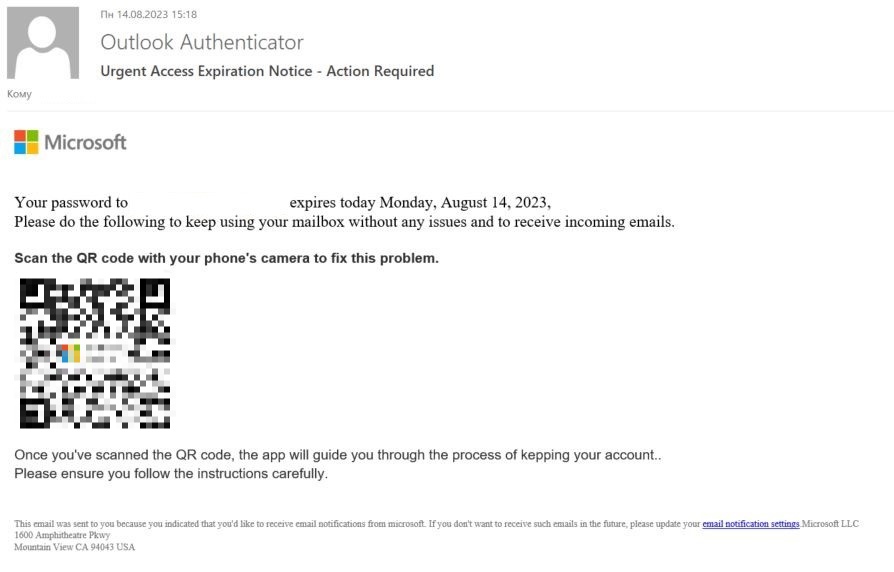 Source: Use of QR codes in email phishing | Securelist
Source: Use of QR codes in email phishing | Securelist
- Parkmobile Payment and Private Information Payment systems are using QR codes to redirect customers to make their payments, this can be commonly found within restaurants and parking vendors. Attackers will cover the legitimate QR code with a malicious code, the attack will redirect the user to a malicious site that can steal credit card and private information.
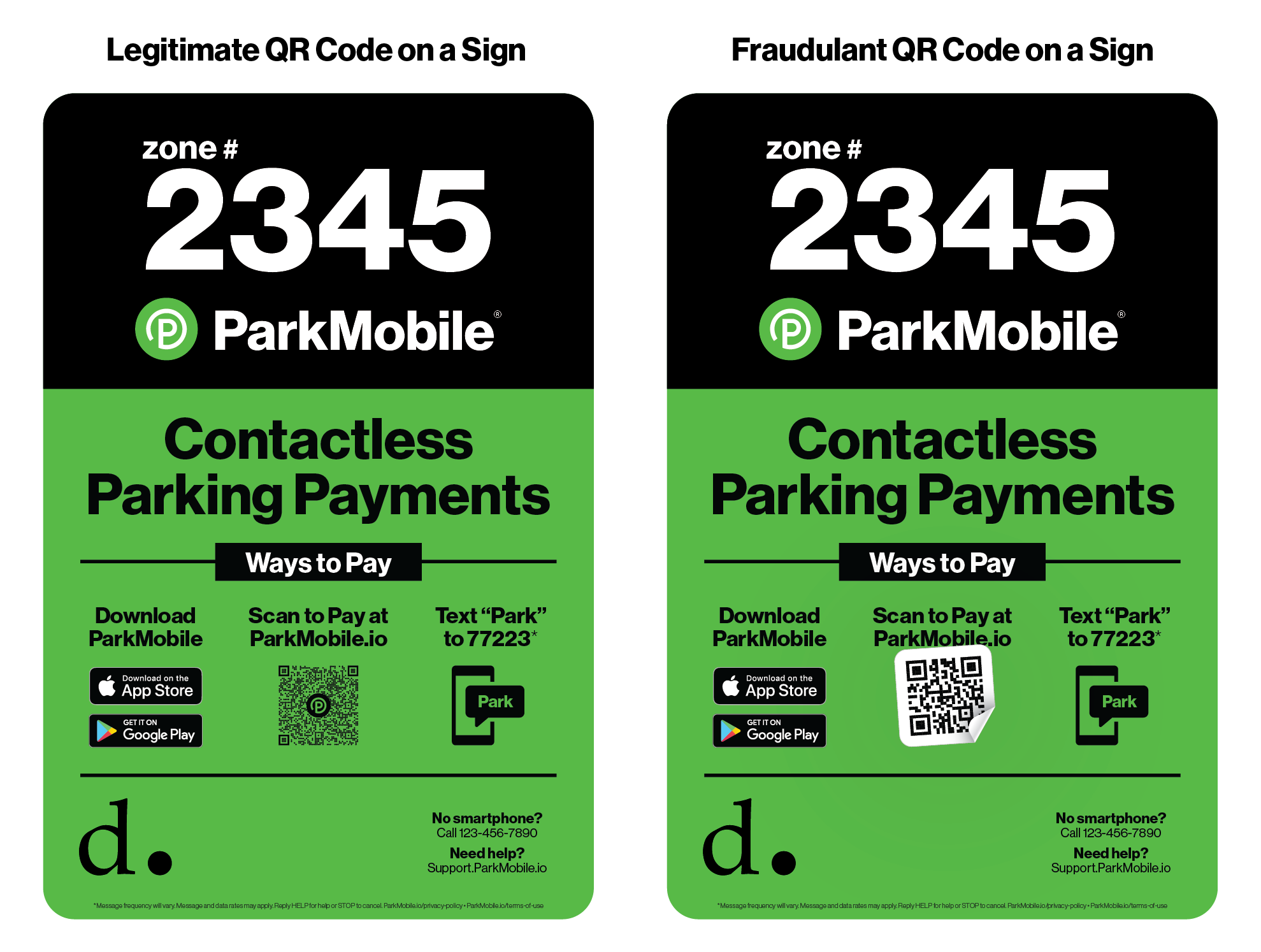 Source: How to Protect Yourself from Scammers when Parking – ParkMobile Support
Source: How to Protect Yourself from Scammers when Parking – ParkMobile Support
How to detect for a phishing emails
- Spelling mistakes.
- Grammatical errors.
- Similar (look-a-like) email address.
- Sense of urgency.
How to reduce QR phishing attacks
- Teach users about the risks and threats of Quishing if possible, use email simulations.
- Preview the QR code link, check if the URL is legitimate or been misspelled to look similar.
- Don’t scan or open QR codes from unknown sources, treat QR codes like any other unsolicited link.
- Scanning a QR code in a physical environment check it has not been tampered with.
- Contact the company the QR code came from and check it was legit.
- Do not download third party app scanners to scan QR codes, use the built-in scanner.